iPhone owners take note: A serious cyber threat is targeting Apple IDs, and it’s more important than ever to be cautious. Security experts at Symantec have uncovered a sophisticated SMS phishing campaign designed to trick you into giving up your valuable Apple ID credentials.
Get security alerts, expert tips – Sign up for Kurt’s newsletter – See the CyberGuy report here
Methodology of attack
Here’s how the scam works: Hackers send text messages that appear to come from Apple. These messages ask you to click on a link for an important iCloud update or verification. Symantec’s research It shows that these links lead to cleverly designed fake websites that ask for your Apple ID and password. To make the site look legitimate, the attackers have also included a CAPTCHA.
Once you complete the CAPTCHA, you are taken to an old iCloud login page where you are asked to enter your credentials. This information is like gold for cybercriminals as it gives them access to your personal and financial data and control over your devices.
Below is an email version of this same scam to avoid. Notice the strange email return address from a non-Apple account, full of dashes and strange characters.
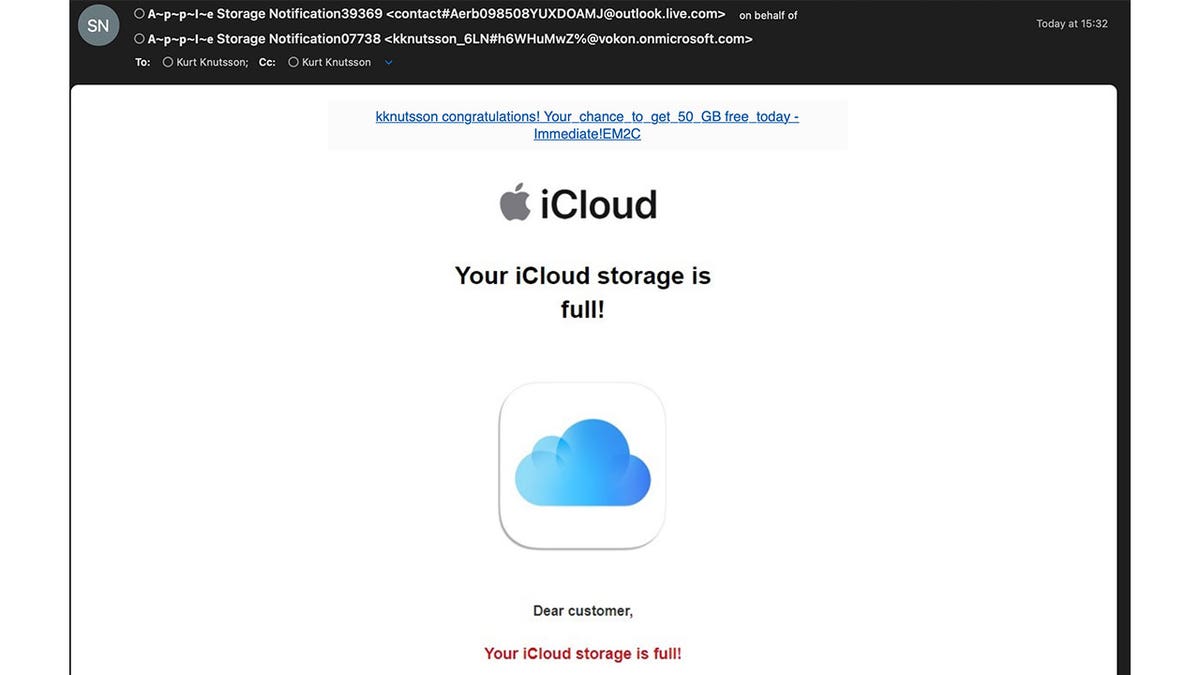
The email scam may claim that the user’s iCloud storage is full. (Kurt “CyberGuy” Knutson)
Apple’s response and protective measures
Apple is aware of these tips and also offers guidelines to help you stay safe. First and foremost, enable two-factor authentication on your Apple ID. This adds an extra layer of security by requiring a password and a six-digit verification code whenever you log in from a new device.
Remember, Apple will never ask you to disable security features like two-factor authentication or stolen device protection. Scammers may claim it’s necessary to solve a problem, but it’s a trap designed to lower your defenses.

The iPhone scam uses text messages. (Kurt “CyberGuy” Knutson)
Recognizing phishing attempts
Phishing scams can be sneaky, but there are ways to spot them. Look carefully at the URL in any suspicious message. Although the message may look legitimate, the web address usually won’t match Apple’s official site. Also, be wary of any text that differs from Apple’s typical communication style.
Symantec highlighted a typical phishing message as part of its warning on July 2. The fraudulent SMS read: “Apple Important Request iCloud: Visit signin(.)authen-connexion(.)info/iCloud to continue using your services.” Strange characters and unfamiliar domains are clear indicators of a scam.

iPhone users should enable two-factor authentication on their Apple ID. (Kurt “CyberGuy” Knutson)
Common scam strategies and how to avoid them
These phishing attempts are not just targeting Apple users. People have reported receiving similar messages from companies like Netflix and Amazon, claiming account issues or expired credit cards. These messages also ask you to click on a link and enter your personal information.
The Federal Trade Commission advises that legitimate companies will never ask for sensitive information via text. If you receive such a message, contact the company directly using a verified number or website rather than the information provided in the text.
7 signs that you have been hacked
How to protect yourself from Apple text and email scams
1) Always use strong antivirus protection on all your devices
This is probably one of the best investments you can make to protect yourself from phishing scams. Having antivirus software actively running on your device will ensure that you are prevented from clicking on any malicious links or downloading any files that will release malware into your device and potentially steal your private information. Read my review of the best antivirus here,
2) Don’t give in to temptation
Scammers often use threatening language to provoke immediate action. Phrases like “act now” or “important” are red flags. Stay calm and be suspicious of any unsolicited messages.
3) Enable two-factor authentication on your Apple device
Implementation Multifactor Authentication This feature on your Apple ID can greatly enhance your security. Always verify the source of messages that claim to be from Apple. If you’re not sure, log in to your account manually via the official Apple website or your iPhone settings instead of clicking on any links.
4) Keep the software updated
regularly Updates Update your operating system, web browser, and antivirus software to ensure they are able to detect and prevent the latest threats. You can regularly check for these updates on your device’s Settings app for software updates, and you can check for updates on individual apps by visiting your App Store or Google Play Store (depending on the device you have). Follow these steps here,
2 bulletproof steps to hack-proof your Mac
What should you do if you clicked on a link and got malware installed on your device?
If you’ve been hacked, it’s not too late. There are several ways you can protect yourself from hackers, even if they have access to your information.
1) Scan your device for malware
First, you’ll want to scan your computer with a reputable and legitimate antivirus program. Check out my expert review of the best antivirus protection for you Windows, Mac, Android, and iOS devices,
2) Change your password immediately
If you have unwittingly given your information to hackers or malicious actors, they can access your social media or banking accounts. To prevent this, you should change the passwords of all your important accounts as soon as possible. However, you should not do this on your infected device, as the hacker can see your new passwords. Instead, you should use Another toolUse devices like your laptop or desktop to change your passwords. Make sure you use strong and unique passwords that are difficult to guess or break. You can also use passwords to change passwords. Password Manager To create and store your passwords securely.
3) Keep track of your accounts and transactions
You should regularly check your online accounts and transactions for suspicious or unauthorized activity. If you notice anything unusual, report it to the service provider or authorities as soon as possible. You should also review your credit report and score for any signs of suspicious or unauthorized activity. Identity theft or fraud.
4) Use identity theft protection
Phishing emails target your personal information. Hackers can use this information to create fake accounts in your name, access your existing accounts, and pretend to be you online. This can cause serious damage to your identity and credit score.
To avoid this, you should use identity theft protection services. These services can track your personal information, such as your home title, social security number, phone number, and email address, and notify you if they detect any suspicious activity. They can also help you freeze your bank and credit card accounts to prevent hackers from using them.
The best part about using some services is that they may include identity theft insurance Up to $1 million to cover damages and legal fees and a white glove fraud resolution team where a US-based case manager to help you recover any losses, Read my review of the best identity theft protection services here,
5) Contact your bank and credit card companies
If hackers have obtained your bank or credit card information, they can use it to make purchases or withdrawals without your consent. You should contact your bank and credit card companies and let them know about the situation. They can help you freeze or cancel your cards, dispute any fraudulent charges, and issue new cards for you.
6) Alert your contacts
If hackers have accessed your email or social media accounts, they can use them to send spam or phishing messages to your contacts. They can also impersonate you and ask for money or personal information. You should alert your contacts and warn them not to open or respond to any messages you send that seem suspicious or unusual.
7) Restore your device to factory settings
If you want to make sure that your device is completely free from any malware or spyware, you can restore it to factory settings. This will erase all your data and settings and reinstall the original version. You should do this Back Up Before doing this, restore your important data and restore it only from a trusted source.
How to delete your personal data from the Internet
Kurt’s Sayings
As cyberattacks become increasingly sophisticated, it’s important to stay informed and vigilant. Protect your Apple ID and personal information by following Apple’s security guidelines and being wary of unsolicited messages. By taking these precautions, you can keep your device and data safe from malicious actors.
Have you ever been a victim of a cyber scam? If yes, what happened and how did you recover from it? Write to us Cyberguy.com/contact,
For more of my tech tips and security warnings, subscribe to my free CyberGuy Report newsletter Cyberguy.com/newsletter,
Ask Kurt a question or let us know what stories you’d like us to cover,
Follow Kurt on his social channels:
Most frequently asked questions answered by CyberGuy:
Copyright 2024 CyberGuy.com. All rights reserved.
















